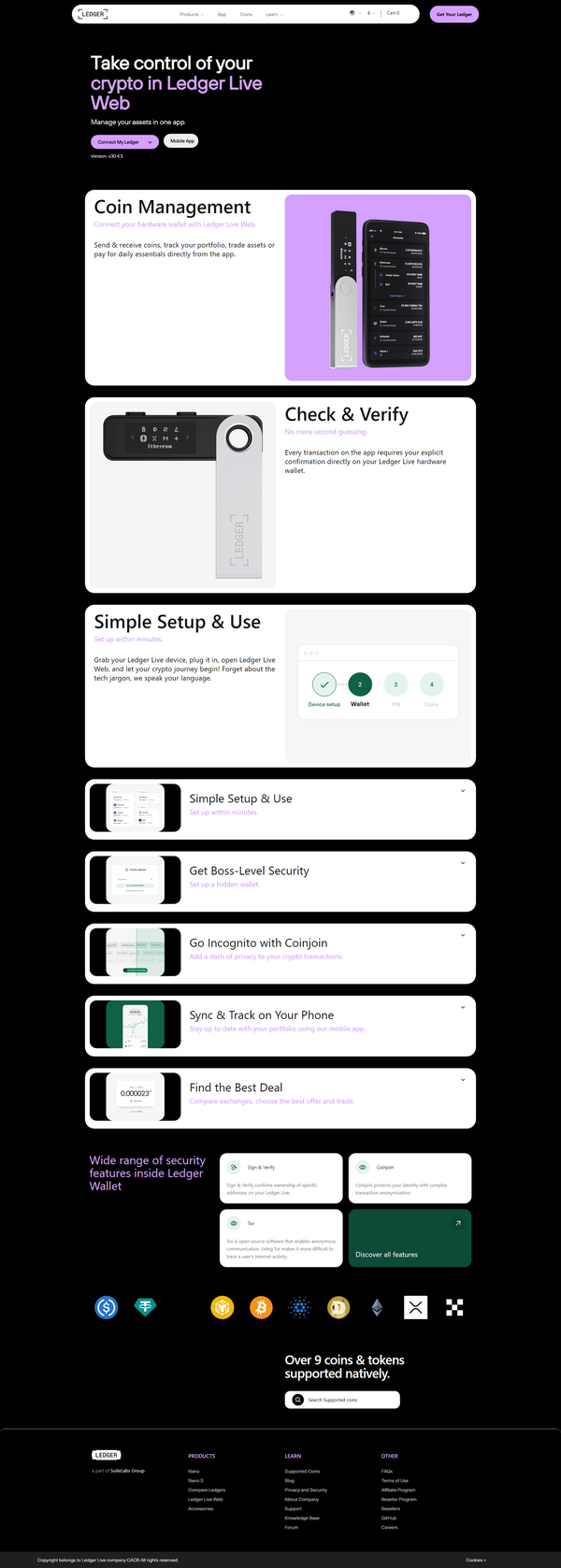
🔐 5 Reasons Trezor Suite is Your Go-To Crypto Dashboard
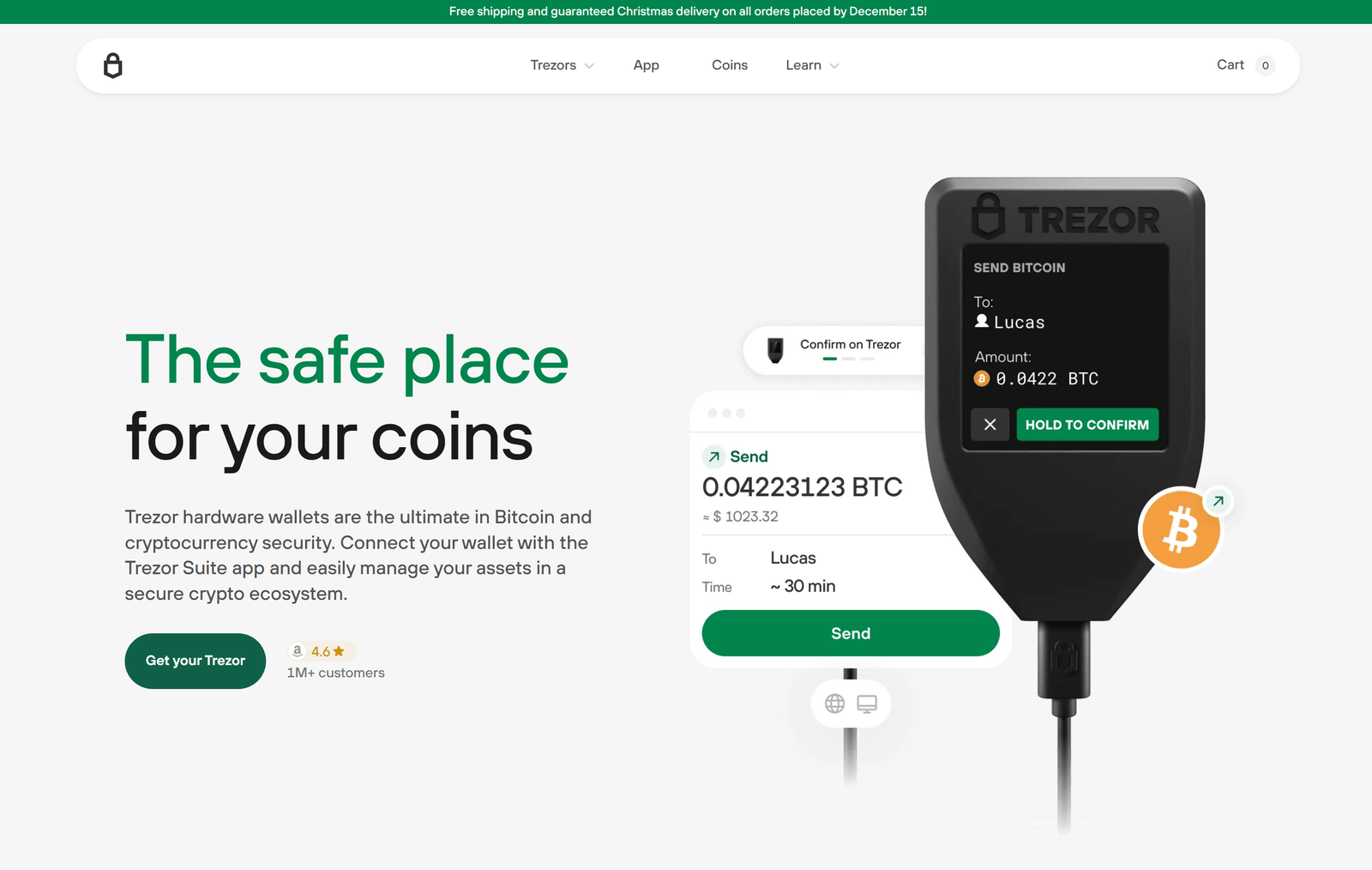
Trezor hardware wallets are renowned for their security, but the Trezor Suite software is the user-friendly application that brings your cold storage to life. Acting as the secure, all-in-one interface, Trezor Suite is where you manage, track, and transact with your crypto assets. It ensures your private keys—the actual control of your funds—never leave your physical device, maintaining the highest level of security while offering the convenience of a modern crypto wallet.
Blog 1: The Secure Gateway to Self-Custody
Trezor Suite: Bridging Hardware Security with Software Simplicity
The primary function of any hardware wallet is to keep your private keys offline, safe from online threats like malware and phishing. Trezor Suite is the official, open-source application that allows you to interact with those offline keys safely.
Unlike typical software wallets, Trezor Suite works in conjunction with your Trezor device. When you initiate a transaction, the request is sent to your connected Trezor, which is the only place your private key exists. The signing of the transaction happens inside the device, and only the signed, non-sensitive data is sent back to the Suite to be broadcast to the blockchain. This physical confirmation on the device's screen ensures that even if your computer is compromised, a malicious party cannot authorize a transaction without your physical consent. It transforms the highly secure concept of cold storage into a practical, everyday tool for digital asset management.
Blog 2: All-in-One Asset Management and Portfolio Tracking
Your Entire Crypto World, Organized and Intuitive
Trezor Suite is designed to be a comprehensive financial hub, eliminating the need to jump between multiple applications. The main Dashboard gives you a clear, centralized view of your entire portfolio, displaying balances and transaction histories across all supported cryptocurrencies and tokens.
This is more than just a balance checker; it is a full-featured management tool. You can easily create multiple accounts for the same coin to segment your holdings (e.g., "Savings," "Trading Fund"), which is a great practice for security and organization. It also handles the complexity of tokens (like ERC-20 tokens on Ethereum), automatically sorting them within your respective coin accounts. For those who want to monitor their funds without connecting their physical device, Trezor Suite even offers a View-only mode using your extended public key (XPUB) to securely track balances.
Blog 3: Advanced Features for Enhanced Control
Beyond Basic Storage: Coin Control, Tor, and More
While its interface is beginner-friendly, Trezor Suite includes powerful features for experienced crypto users focused on privacy and precision. One standout feature is Coin Control, which is particularly relevant for Bitcoin users. It allows you to manually select which unspent transaction outputs (UTXOs—essentially, specific bundles of crypto you've received) to use in an outgoing transaction. This offers greater control and can be used to improve transaction privacy by avoiding linking certain funds together.
For even deeper privacy, the Trezor Suite integrates Tor (The Onion Router) support, which routes your internet traffic through a decentralized network to obscure your IP address and make your online activity harder to trace. Additionally, it supports advanced backup schemes like Shamir Backup (on Trezor Model T), which can divide your recovery seed into multiple shares for ultimate protection against loss.
Blog 4: Trade, Stake, and Grow Your Portfolio Securely
Built-in Trading Services: Buy, Sell, and Stake
Trezor Suite has integrated services that allow you to buy, sell, and swap cryptocurrencies directly within the application, often in partnership with verified third-party providers. This functionality streamlines the process of acquiring or exchanging assets while maintaining the security guarantee of your hardware wallet. When you use these services, the funds are sent directly to an address controlled by your Trezor, keeping you in self-custody from the very start.
Furthermore, Trezor Suite supports staking for certain Proof-of-Stake cryptocurrencies like Ethereum (ETH) and Cardano (ADA), enabling users to earn rewards on their holdings without ever having to move their private keys off the device. This integration of core crypto functions transforms the wallet from a mere vault into an active financial tool.
Blog 5: The Open-Source Security Advantage
Transparency and Trust: Trezor’s Commitment to Open-Source Code
Trezor's entire ecosystem, including the Trezor Suite software and the device firmware, is open-source. This is a fundamental principle of cryptocurrency security: the code is publicly available for anyone—from security experts to the general community—to review, audit, and verify.
This radical transparency is a critical security feature, as it allows for the crowdsourced detection of potential vulnerabilities, eliminating the need to blindly "trust" the manufacturer. Coupled with mandatory PIN protection, an optional passphrase for hidden wallets (which adds a layer of deniability and extreme security), and on-device transaction verification, Trezor Suite provides a robust and auditable security framework that empowers users to truly own their digital wealth.
For a comprehensive guide on managing your coins and tokens securely, you can watchHow to Setup & Use the Trezor Safe 7 (BEGINNER'S GUIDE). This video provides a detailed walkthrough of the initial setup and basic usage of a Trezor device, which is primarily managed through the Trezor Suite app.